Why Privacy Matters
Privacy and decentralization counter surveillance and centralization. While centralization easily leads to surveillance and corruption, more privacy can help regain personal and financial autonomy. Read on to discover the costs of living with no privacy and how technology can restore it.

Bottom Line: One‑Minute Summary
- Power corrupts: Individuals in power inherently drive self-interest over collective well-being (Milgram, Stanford Prison Experiment, neuroscientific studies).
- Centralization drives power accumulation and surveillance: The more power individuals and institutions have, the higher the degree of corruption. Transparency in centralized systems often enables control rather than accountability, as seen in data aggregation by tech giants and governments.
- Decentralized systems built on privacy prevents corruption: Privacy is a key building block in decentralized systems that protects individual autonomy, preventing manipulation, financial exclusion, and personal safety risks.
- Costs of no privacy:
- Personal Safety: Crypto holders are targeted by criminals, with centralized exchanges exposing data to hacks or state actors.
- Financial Autonomy: Debanking, erroneous flagging, and surveillance pricing (e.g., Orbitz, Target) exploit users’ lack of privacy.
- Free Speech: Censorship and self-censorship under mass surveillance (e.g., Germany’s legal crackdowns, NSA programs).
- The Path Forward:
- Prioritize Privacy-by-Code technologies over Privacy-by-Compliance laws, which fail to stop surveillance or create innovation.
- Examples of use cases:
- Anonymous crypto transactions: Tools like Railgun or Privacypools enable anonymous transactions while proofing the funds do not originate from illicit sources.
- Secure cloud computing: Fully homomorphic encryption allows processing of encrypted data in the cloud, ensuring no exposure of sensitive information.
- Encrypted healthcare data sharing: Joint research and AI training on clinical/genomic data while preserving patient confidentiality.
- Censorship-resistant voting: Zero-Knowledge Proofs enable verifiable, anonymous ballots that protect voter privacy and prevent tampering.
- Key Takeaway: Decentralization and privacy are the natural antidote to centralized power, leading to a more stable society where individuals retain self-control and can't get easily manipulated by corrupt institutions.
How It Started
I first heard about Bitcoin on a sailing trip in 2014. I was most intrigued by Bitcoins decentralized design, which guarantees a fixed supply that cannot be inflated by central banks. At the time, I was in disbelief how central banks gained control over the money supply, creating a system that expropriates the majority silently through inflation. I began following Andreas Antonopoulos, the real “Bitcoin Jesus,” whose insights on the transformative potential of cryptocurrencies in a world where "power corrupts" resonated with me. His perspective made me question how power should be distributed to best advance humanity and what role cryptotechnologies can play to reduce corruption.
The Corrupting Influence Of Power
Research shows how power often drives individuals to prioritize self-interest over collective well-being. Several studies highlight the antisocial effects of concentrated power.[1] Classic psychological experiments strengthen this view: Milgram’s Obedience Experiment (1960s) revealed how people comply with authority even when doing so harms others, and the Stanford Prison Experiment (1971) demonstrated how quickly power can spiral into abuse.[2] Neuroscientific studies further indicate that when people feel powerful, their brains become less responsive to the emotions of others.[3] In essence, once power is concentrated, corrupt behavior becomes almost inevitable.
The Danger Of Centralization And Transparency
While transparency is often associated as a safeguard, in centralized systems it can instead serve as a tool for surveillance. Humans are inherently self-interested, and as Vitalik Buterin explains using game theory, a value-maximizing individual strives to the combination of absolute power and maximum transparency (dictatorship). In this context, absolute power means complete centralization, where decisions are made without adequate checks by an individual or institution. Instead of exposing corrupt actions to accountability, excessive transparency can be manipulated to further increase corruption. Procurement illustrates how more transparency leads to more corruption: When bidders know who the key decision‑makers are, collusion follows: pre‑tender negotiations and covert agreements push contracts toward favored firms, often sidelining lower‑priced or higher‑quality alternatives. This creates a vicious cycle: as more data is collected and transparency increases, power grows, fueling corruption which further reinforces centralization and directs even more surveillance.
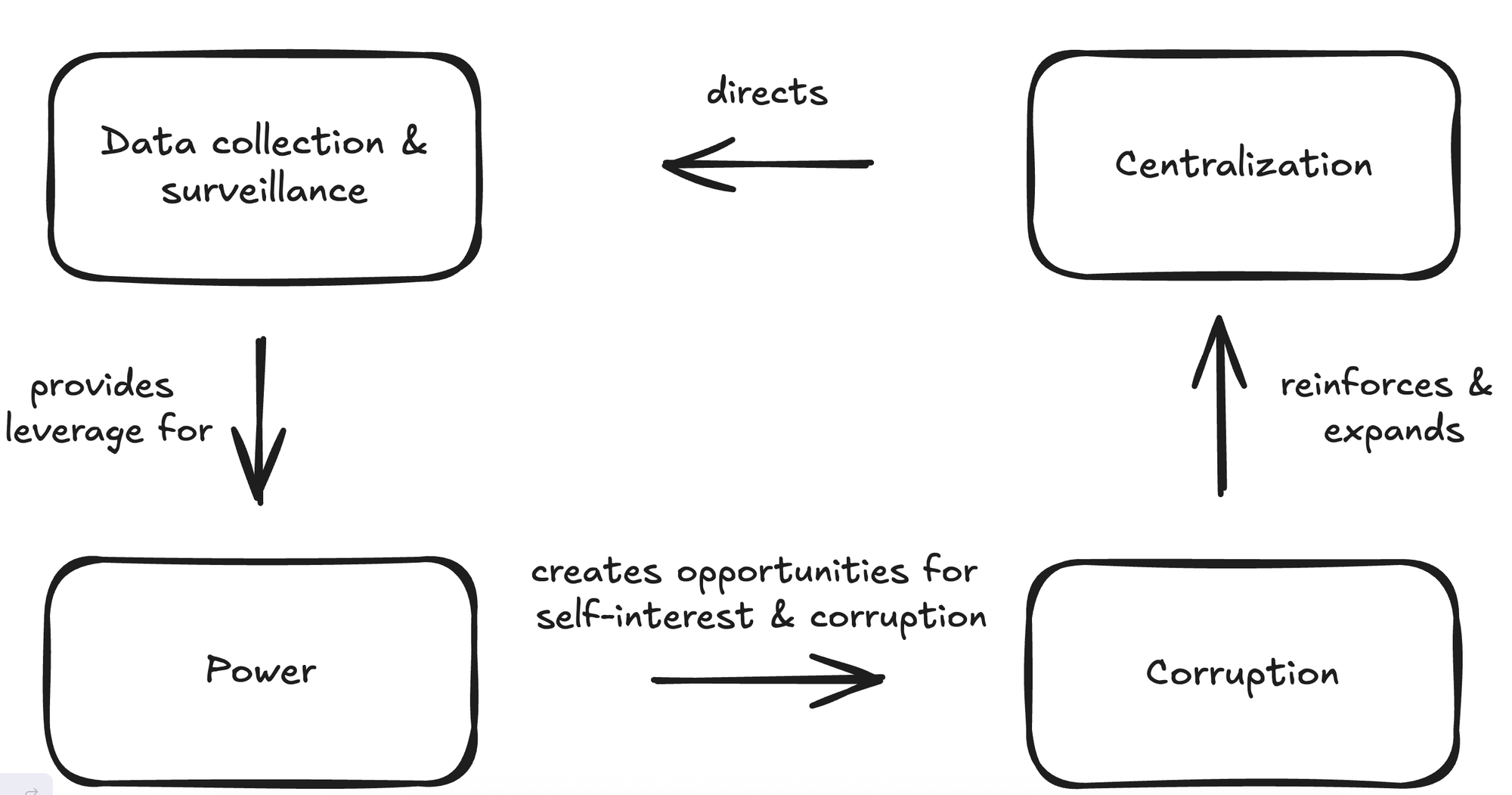
The Importance Of Decentralization And Privacy
Decentralization is the natural antidote to centralization of power. By making it harder for a single actor to accumulate power, decentralized systems help maintain individual autonomy. Satoshi Nakamoto, the anonymous creator of Bitcoin, understood this well. By choosing to remain anonymous, Satoshi ensured that Bitcoin could develop without the interference of any centralized authority.
Privacy allows participants to act freely, free from external coercion and undue surveillance. Eric Hughes defines privacy in the Cypherpunk's Manifesto as the power to selectively reveal oneself to the world. This “power” is precisely what makes a truly decentralized ecosystem possible: it protects personal autonomy against manipulation attempts by centralized institutions seeking to gain or maintain control.
In a stable society, power is largely decentralized and individuals have privacy. Research shows that when people experience genuine control over their lives they are more empathetic, prosocial, and resistant to manipulation.[1:1] Privacy strengthens personal control and makes manipulation harder.
That said, centralization and transparency are not all bad and offer real advantages: Economies of scale, network efficiency, and accountability among them. The key is to centralize at the minimum effective dose. History teaches us that centralization morphs into domination and transparency easily slides into surveillance.
Privacy Over Time
"Even if you're not doing anything wrong, you are being watched and recorded" - Edward Snowden
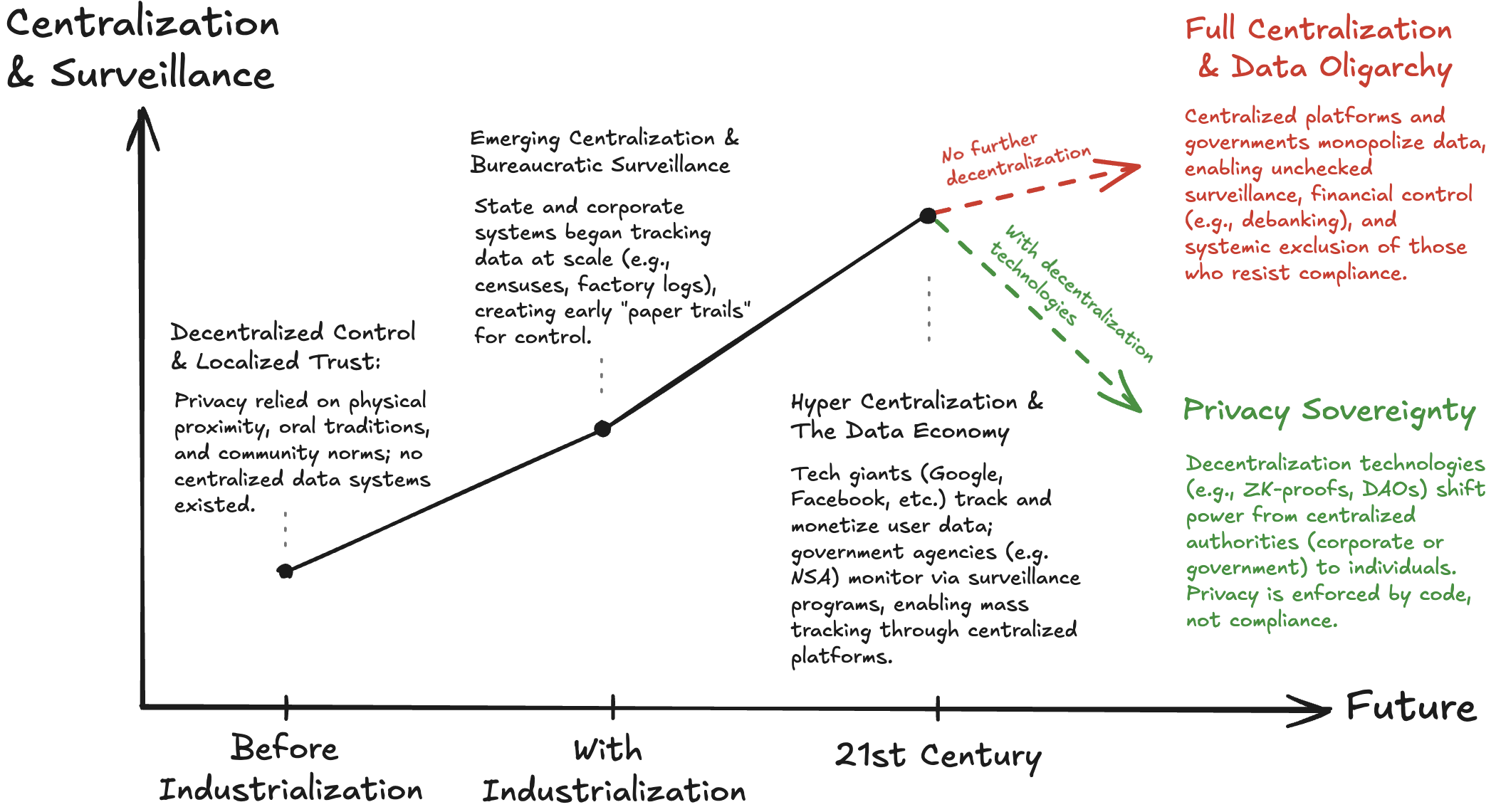
Our technological improvements since the industrialization has accelerated centralization, bringing with it all its benefits. However, this centralization has also led to highest levels of surveillance. Today, we find ourselves in a situation where a handful of tech giants and centralized institutions hold vast amounts of personal data about us. This data is not only already being exploited but is also at risk of being fatally misused, especially in the event of a regime change.
One of many historical examples is the experience of Jewish citizens in the Netherlands during World War II. The dutch pre-war registration of names, addresses, and religions, later enabled Nazi occupiers to quickly identify and target Jewish individuals, contributing to the tragic loss of 73% of the Dutch Jewish population. This serves as a strong reminder that our shared personal data and the level of surveillance we endure can become significant liabilities. An authority that does not harm you today based on your data may do so tomorrow.
Our current hyper-centralized environment raises serious concerns about privacy and the emergence of a data oligarchy, where a few entities hold immense power over our lives.
Yet, there is hope. The concept of "Privacy Sovereignty" envisions a future where decentralized technologies empower individuals to reclaim control over their data, challenging the prevailing trends of centralization.
Looking ahead, we have an important choice: we can either continue with centralization and surveillance, which, at this point, provide few benefits and raise the risk of corruption, or we can embrace decentralization and enhanced privacy as a guard against the human tendency to misuse power.
The Costs Of No Privacy
When Naval Ravikant said: “You want to be rich and anonymous, not poor and famous," he was pointing out that wealth and your level of privacy together determine your (quality of) life and autonomy. Especially in crypto, associating your identity with substantial holdings raises the likelihood of cyberattacks, phishing, social-engineering exploits, and even physical assault. Maintaining anonymity is the single most effective security measure.
1. Personal Safety
When your crypto holdings make you a target:
- Criminals target crypto holders: High-profile cases like the kidnappings of David Barrant (co-founder of Ledger) and Dean Skurka (CEO of WonderFi) are not outliers. Organized crime groups now actively surveil social media, forums, and even public blockchains to identify wealthy individuals. Even if you’re not a “public figure,” casual mentions of your crypto activities online or among your contacts and "friends" can mark you as a target.
- I never told anyone about my crypto activities, so I am safe? Not so quick. Have you ever used centralized exchanges (CEXs) like Kraken, Binance or Coinbase? They store your personal data, transaction history, and location. All it takes is one more of the dozens hacks, or one corrupted employee, and your data becomes public. We know that secret services agents from North Korea are trying to undermine CEXs.[4] We can only guess how many of them are already undermined.
The takeaway: (1) Keep a low-profile and anonymize your crypto holdings or (2) if you decide to stay visible, plan for the worst case and actively manage your personal and your family's safety.
2. Financial Autonomy
Centralized institutions control whether you can be part of our traditional financial system. If they exclude you, it's nearly impossible to participate normally in society or to run business:
- Debanking as a tool of suppression: Marc Andreessen spoke about crypto founders being systematically debanked. Financial institutions, under pressure from political agendas, freeze accounts, block transactions, and deny services.
- Unbanked: Of the 1.4 billion unbanked people, 332m people are systematically excluded from banking by not fulfilling compliance documentation criteria.[5]
- Erroneous flagging: I’ve seen friends with Wise accounts get blocked for weeks over “security checks”. When your financial activity is monitored and you need permission from the centralized institutions to participate, you lose autonomy. Your money isn’t yours if it can be frozen or taken away without cause.
The takeaway: Prioritize decentralized, permissionless services to reduce reliance on centralized institutions. However, most of us still depend on them for daily life. While you’re tied to centralized institutions, stay low-profile to avoid becoming a target, and diversify your assets across jurisdictions and asset types to mitigate risk.
3. Freedom of Speech
Increasing surveillance chills dissent:
- Censorship: In Germany, individuals face prosecution for sharing memes on social media, with former Vice Chancellor Robert Habeck and other politicians actively pursuing legal action against critics in more than 1,000 cases. This misuse of law enforcement to silence dissent is a serious concern about free speech.
- The Chilling Effect: The chilling effect happens when fear of surveillance stops people from accessing or sharing information, even if it’s lawful. Example: "Edward Snowden disclosed in 2013 that the US government's Upstream program was collecting data on people reading Wikipedia articles. This revelation had significant impact on the self-censorship of the readers, as shown by the fact that there were substantially fewer views for articles related to terrorism and security".
The takeaway: If you critique power or expose information that challenge special interests, expect surveillance or retaliation. Stay anonymous and use decentralized, censorship-resistant channels to speak freely.
4. The Hidden Ways Institutions Profit from Your Lack of Privacy
Companies and government agencies are surveilling you for their own benefit of maximizing profits and suppressing people with dissenting opinions.
When value-based pricing becomes "Surveillance Pricing"
If you’ve ever studied how to price a product or service, you know that simple cost-plus formulas (cost basis plus markup) usually leave money on the table. Since companies exist to maximize returns, they turn to value-based pricing: charging each customer exactly what their data indicates they’re willing to pay. The result? You end up paying more than you would if you were anonymous. Even worse, value-based pricing requires vast amounts of personal information, and businesses will exploit every opportunity to collect it, legal or not, with or without consent. Welcome to “surveillance pricing”.
- Orbitz used user-device data (e.g., Mac users) to show pricier hotel options, charging more for the same service based on inferred spending habits.
- Target priced TVs higher for users near stores, exploiting proximity data to extract more from those willing to pay.
The more companies know about you, the more they can manipulate prices to your disadvantage.
Big Techs data harvesting machine
Google and Apple systematically collect user data through opaque practices, without clear consent or transparency:
- Google’s voice assistants records private conversations (e.g., medical or domestic discussions) to refine ads, with contractors accessing sensitive content for "quality control."
- Apple’s iCloud backups, automatically enabled for most users, allow law enforcement access to personal data like photos and chat logs, despite claims of strong encryption.
Government agency surveillance: Power without accountability
Government agencies like the NSA misuse surveillance tools to monitor billions of people under the guise of "national security":
- NSA’s bulk data collection: Programs like PRISM and XKEYSCORE allow the agency to harvest metadata (e.g., who you communicate with, when, where) from tech giants like Google, Apple, and Meta, often without user knowledge or consent. As of 2025, the programs likely continue to operate. I can't find any evidence of the programs being stopped or regulated.
- The FBI has violated the privacy rights of tens of thousands of Americans by misusing warrantless surveillance practices under Section 702 of the Foreign Intelligence Surveillance Act (FISA), allowing extensive backdoor searches of Americans' and non-Americans' communications without proper legal oversight. Additionally, the US government is actively pressuring big tech companies (Apple, Google, Microsoft, Meta, etc) to create backdoor access in their software products, leading to concerns that these companies may comply with such requests.
Criminals use public information about crypto holders for assault, corporations are gouging prices, Big Tech is secretly collecting and monetizing personal data, and government agencies are mass surveilling us. All driven by profit motives and the desire to sustain existing power structures at the expense of individuals.
The key in reversing this trend is more privacy instead of even more transparency leading to more surveillance.
Outlook On Privacy
Today’s Privacy-by-Compliance laws (GDPR, CCPA, and others) set out rules for handling personal data. In practice, they often fail to protect us. Many companies do not have the resources or the incentive to follow the policies. Enforcement is weak and uneven. The regulators that write these rules are heavily influenced by corporate lobbyists and political interests. Those groups favor data aggregation over true privacy. When power shifts or new authorities take charge, “protected” data can be used for surveillance, manipulation, and control.
This ineffective model produces two harmful outcomes:
- Stifled innovation: Companies pull back from data-driven research and development (e.g. in healthcare) for fear of non-compliance, and users hesitate to use cloud services that could otherwise improve performance and convenience. Result: Slowdown in technological progress.
- Unchecked surveillance: Corporations and governments continue to amass massive data stores. Tracking, profiling, and algorithmic discrimination run unchecked. Result: Users lose control about their personal data and face new forms of abuse.
Privacy-by-Code to the rescue!
Privacy-by-Code embeds cryptographic protections directly into system architecture so that data leaks are impossible by design. Instead of relying on after-the-fact penalties, these techniques enforce privacy rules automatically:
- Full data ownership: Only you hold the decryption keys. No company or regulator can read, share, or delete your data without your explicit consent.
- Privacy-preserving data use: Companies perform analytics on encrypted data and deliver services without technical ability to access or store personal data.
- Immutability: Data privacy is enforced by code and hardware. Political shifts, corporate lobbying, or new laws cannot override our privacy settings.
Vitalik Buterin mentioned three key technologies that help us achieve programmable cryptography:
- Zero Knowledge Proofs: Prove anything (even extremely complex computations) about data you hold, without revealing the data itself.
- Fully Homomorphic Encryption: Do any computation on encrypted data without being able to learn anything about the data.
- Obfuscation: Convert any program into an encrypted program that does the same thing but doesn’t expose its inner workings.
These technologies would allow us to advance in several fields:
- Identity & Reputation: Prove attributes (age, citizenship, professional license, “no criminal record,” etc.) via Zero Knowledge Proofs without ever revealing underlying documents or personal data.
- Finance: Transact anonymously with crypto, and proof at the same time that the funds are not illicit (Railgun, Privacypools).
- Governance: Cast ballots on a public ledger with Zero Knowledge Proofs ensuring each vote is valid but unlinkable to your identity, end-to-end auditable, and tamper-proof.
- Healthcare: Use encrypted clinical and genomic data to power joint studies, train AI models, and uncover treatments without exposing raw patient records.
- Cloud: Process your data in the cloud under fully homomorphic encryption so only you can decrypt results, enabling unlimited scale and performance with zero privacy trade-offs.
While some use cases like Railgun or Privacypools are already operational, others remain in development.
What you can do until privacy technology catches up
-
Now:
- Stay private: Be very cautious about what data you share publicly, especially data regarding your wealth or indicating off the mainstream political opinions.
- Run computation locally whenever possible: Use local AI models (LLMs), and other tools like no-log VPNs, TOR browser, end-to-end encrypted emails, and messengers. Keep your data private as much as you can. Data you share now might be stored indefinitely on third party servers.
- Diversify your financials: You will likely not be able to completely escape our traditional financial system, but try to build a second leg: Hold and use crypto anonymously (e.g., Railgun, Privacypools). Buy critical goods and services anonymously (e.g., pay for your VPN and eMail provider with Monero).
-
Future:
- Homomorphic encryption will enable you to run computing in the cloud without privacy concerns.
- Permissionlessly participate in financial systems, transacting anonymously while using Zero-Knowledge proofs to verify your legitimacy (e.g., “I’m a person, and my funds are not illicit”) without exposing sensitive details. This would enable true financial autonomy, allowing you to engage in transactions securely and privately, free from centralized surveillance or control.
About me
I’m Cassius Nox, an entrepreneur with a finance background who spent a decade building a data company that took me to three continents.
I have been fascinated by humanity’s journey toward becoming a star‑faring civilization. I see systematic abuse of power and corruption as major roadblocks that choke innovation and undermine our progress.
Privacy and crypto are the antidotes: by reclaiming control over our autonomy and finances, we can innovate freely, and it becomes far harder for any one entity to misuse power.
My aim is to show you the path to privacy, equipping you with the tools to protect your personal and financial autonomy. The more people prioritize privacy, the stronger we are against authoritarians, ensuring the freedom that fuels innovation.
Questions, ideas, or feedback? Reach me at cassius.nox@tuta.com.
Cislak, A., Cichocka, A., & Wojcik, A.D. (2019). Power corrupts, but control does not. Social Psychological Bulletin. https://pmc.ncbi.nlm.nih.gov/articles/PMC5971364/ ↩︎ ↩︎
Milgram, S. (1963). Behavioral study of obedience. Journal of Abnormal and Social Psychology, 67(4), 371–378. https://doi.org/10.1037/h0040525
Zimbardo, P. G. (1971). The Stanford prison experiment: A simulation study of the psychology of imprisonment. American Psychologist, 26(11), 676–682. Link to study on Google Scholar ↩︎Muscatell, K.A., Morelli, S.A., Falk, E.B., Way, B.M., Pfeifer, J.H., Galinsky, A.D., Lieberman, M.D., Dapretto, M., Eisenberger, N.I. (2012). Social status modulates neural activity in the mentalizing network. Neuroimage, 60(3), 1771–1777 https://pmc.ncbi.nlm.nih.gov/articles/PMC3909703/ ↩︎
Kraken (2023). How we identified a North Korean hacker. https://blog.kraken.com/news/how-we-identified-a-north-korean-hacker ↩︎
Coinlaw (2025). Unbanked population statistics. 23 % of the 1.4 bn unbanked adults worldwide lack the necessary documentation to open an account. https://coinlaw.io/unbanked-population-statistics/ ↩︎
